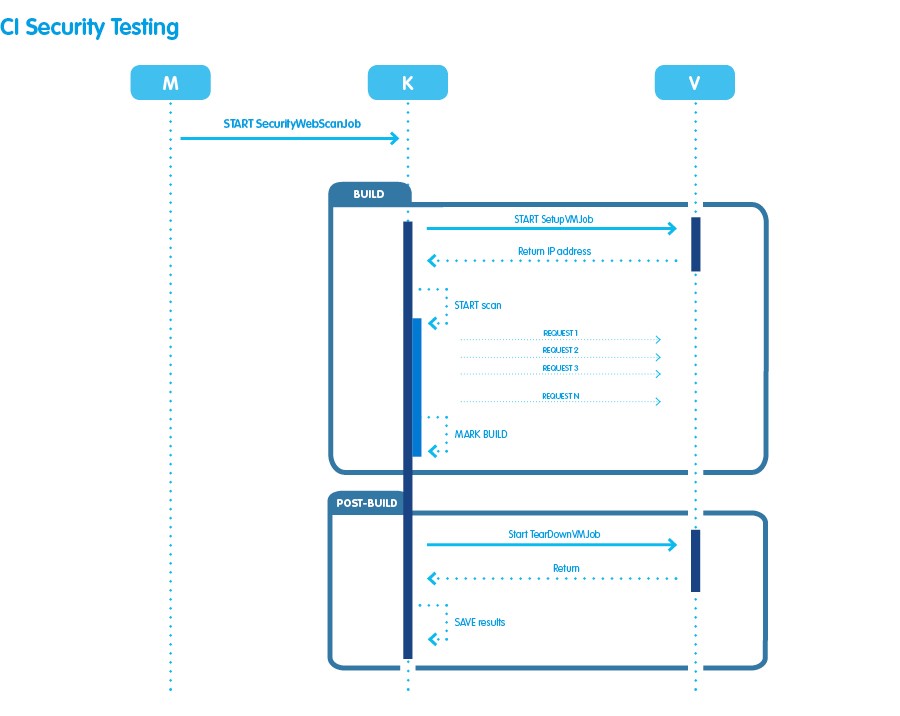
As can be seen from the diagram, three nodes are involved in the process:
- M: Jenkins’ master node;
- K: a new machine on which we have installed our web scanner and will be our slave node where the job that governs the scan will be performed;
- V: another Jenkins slave node where the setup and teardown jobs that will be discussed later will be performed.
Furthermore, within V, we prepared a snapshot of a virtual machine with an Imagicle UCX Suite configured and pre-populated with data to facilitate the work of the “spiders” in finding the pages to be scanned for vulnerabilities.
Let’s see how the complete cycle works. First, the master node starts the job dedicated to safety tests, which, in turn, starts the setup job. Then, the latter updates the virtual machine that will be used for testing.
Now:
- the previously prepared snapshot is restored;
- all Windows Updates are made with the necessary restarts;
- the installation of the latest package created by the master branch of our repository is launched;
- once the installation is successfully completed, the setup job communicates the IP address of the web portal.
At this point, the security test job knows the IP address, and through the REST services exposed by the web scanner, the scanning starts by sending a payload with the necessary information (IP address, configurations to be used, any exclusions).
The scan consists of two stages:
- a first phase of “discovery” of the web pages;
- a second phase in which the pages found are tested to check for any vulnerabilities.
As soon as the scan finishes, the security job marks the current build consistent with the scan result:
- SUCCESS, if no vulnerabilities of the configured severity and confidence have been detected;
- FAILURE, if vulnerabilities have been detected.
The process ends by starting the teardown job which takes care of turning off the virtual machine just under test. In addition, information about the scan that has just finished is archived. This way, you can review any details of the vulnerabilities found.
The cycle described lasts about 5 hours and on average, about 150 thousand requests are sent to the suite.
On the R&D side, this integration has allowed us first of all to obtain a considerable saving of time. Now it is Jenkins who takes care of all the time-consuming activities: updating the environment, starting the scan and producing the results. This allows developers to focus on more important activities such as analysis and development. Furthermore, if potential vulnerabilities are detected by the security scan, the time saved can be invested in studying and solving the critical issues found.
Automated scanning has a number of benefits compared to a manual scan:
- duplication of tests performed is avoided;
- the application is tested for a greater number of vulnerabilities;
- a test standard is created, regardless of the user’s ability.
All this translates into a saving of resources, as well as ensuring that the application is tested for all critical issues covered by the web scanner.
 Register
Register
 Register
Register
0 commenti